The President, H.E. Nana Akufo-Addo on the 23rd October 2017 at the sidelines of the Ghana National Cybersecurity Week, inaugurated the National Cybersecurity Inter-Ministerial Advisory Council. This singular action signalled and kicked in the process of formalising and securing Ghana’s Cyberspace. With support from the World Bank (WB), a National Cybersecurity Policy and Strategy (NCSPS) has been developed, and currently, the Ministry of Communication is working on relevant aspects of; capacity building, cybercrime legislation, standardisation and safeguards which when completed would lead to the operationalisation of the NCSPS. Given the importance of the NCSPS to Ghana’s security, economy and international peace, it is essential that such a policy is thorough and captures at best the crucial cyber ecosystem matters exhaustively. The comprehensiveness of NCSPS would undeniably contribute immensely towards its success. It is in this regards that I offer some perspective on NCSPS. Before delving into issues in the NCSPS, it will not be out of place to take a bird view of Cybersecurity from the global standpoint.
Global Cybersecurity developments
The world today is witnessing an unprecedented expansion in web connectivity due mainly to the significant improvements in information and communication technologies. The borderless exchanges of information via the internet and the web between individuals, organisations and states have reached unprecedented levels. These tools of communication have boosted trade and commerce, knowledge sharing and international diplomacy. The development is, however, not without challenges. The wave of interconnectivity through these modern information technologies have equally exposed the world to a wax of complex and transnational threats concerning the cyberspace. The cyberspace threats which involves the use of computer technologies to deliberately disrupt an individual, organisation or a nation’s information systems have since become a worrying development for the world. They have become a widespread occurrence, and according to Center for Strategic and International Studies (CSIS), cybercrimes cost about USD 40.0 billion to the global economy annually.
Recent famous cyber-attacks in the international space include the attack on Sony Pictures Entertainment, German Parliament, Ukraine Power Grid, and World Anti-Doping Agency and so on. In all these attacks personal information of citizens got compromised, vital information stolen, and often destabilised the functioning of critical and defense infrastructure systems of the attacked individual, organisation or nation.
Cybercrime is a growing threat and is a significant concern due to its subtilty and remoteness. It requires not a massive military force for invasion but, technological prowess of a country or a group or individuals to penetrate their identified targets infrastructure. It can be carried out by a small nation against a mighty one. The perceived implausibility of war breaking up in the 21st century due to the interconnectedness of humanity suddenly is under threat from the potentiality of cyber-warfare. Like other global concerns, activities relating the cyberspace have received considerable attention in the international discourse.
Cybersecurity – the activities aimed at protecting information and systems with appropriate protocols of technological security measures – has since become a multi-billion industry as countries, organisations and individuals seek remedies from potential cybercrimes.
Among the international efforts at attenuating the debilitating impact of cyber-related attacks is the applicability of international law to issues of cyberspace albeit weak enforcement. International law principles apply, and equally important are individual national policies which ultimately support the international law in ameliorating the global impact of cybercrimes. To galvanise support for international efforts, at the 2016 G7 Summit held in Ise-Shima, Japan, the leaders unanimously endorsed the G7 Principles and Actions on Cyber without dissent. The G7 Principles and Actions on Cyber primarily is meant to promote and protect open, interoperable, reliable and secure cyberspace.
In specifics, the G7 leaders agreed to take strong action against the malicious use of cyberspace, discouraged nations from conducting activities that promoted theft of intellectual properties, reaffirmed the applicability of international laws, promote a strategic framework of global cybersecurity and finally to promote a multilevel approach to internet governance. The Summit also birthed a new working group on cybersecurity, which is mainly responsible for ensuring enhanced policy coordination and cooperation among the G7 Countries to promote global stability of the cyberspace as well as providing security of cyberspace ecosystem.
Despite the firm commitment of world leaders and the United Nations (UN) towards the efforts at reducing cyber-attacks, the situation has not gotten any better. Given the consequential implications of cyber-attacks, various national governments have been working assiduously at devising strategies to ensure threats are reduced to barest levels and at the same time contribute towards the global efforts. Advanced Countries have over the past two decades devoted significant resources towards cyberspace issues. Countries like the United States and Israel have been at the forefront of cybersecurity technology developments and are reaping good returns on such investments. For instance, in the year 2016, Israeli cybersecurity companies made revenues in excess of 8.0billion USD from the sale of cybersecurity technologies. Israel is one of the few countries that has been able to turn cyber-related threats into a business opportunity and have made a good fortune from the trade.
Cyberspace of Ghana
Ghana has had its share of cyberspace attacks and continues to experience such threats routinely. In 2016, according to Mr Dele Aden, the Managing Director of Delta3 International, Ghana lost a total 50.0million USD to cyber-related attacks. In Africa, the figure was about 2.0 billion USD –(GhanaWeb). It, therefore, very much in place for the government to seek remedies to such menace.
In this regard, the NCSPS has been developed, National Cybersecurity Inter-Ministerial Advisory Council has been established, and the government has also rectified many international and regional conventions relating the cyberspace ecosystem. The development is exciting and vital and very timeous given the fact that government is pushing many reforms which are delivered on the platform of technology. These initiatives which include the national identification system project, the digital addressing system, e-payment systems, digital financial services programme, as well as the many e-government initiatives, increase the exposure of the country to possible cyber attacks.
The government efforts so far are commendable. Certainly, there is room for improvement and the government must be encouraged to do more to secure the people of Ghana sufficiently and at the same time contribute towards global efforts at attenuating the canker. I, therefore, wish to share some few thoughts on the NCSPS by drawing on comparison with best practice elsewhere. The objective is to contribute towards the betterment of the NCSPS by way of increasing its potency, relevance and sustainability.
Thoughts on the NCSPS
- My first thought on the NCSPS is on the stakeholder arrangement. It appears to me that the Ministry of Communication is the driver of the NCSPS. If the observation is right, then the NCSPS would suffer implementation challenges. Cybersecurity goes beyond Communication and has broader stakeholder groups. For instance, in Japan, under the Basic Act and Cybersecurity Strategy of 2015, the National Center for Incident Readiness and Strategy for Cybersecurity (NISC) got established to facilitate the activities concerning Japan’s cyberspace. The NISC is sufficiently empowered to make recommendations to the various organs of government directly and is under the Cabinet Office. The Chief Cabinet Secretary chairs the Cybersecurity Committee with membership drawn from the Cybersecurity Strategic Headquarters and the National Public Safety Commission. The rest are; Internal Affairs and Communications, Foreign Affairs, Economy, Trade and Industry, Defense, Information Technology Policy, as well as several experts from diverse backgrounds.
The functions of NISC is in twofold; a) monitoring of national agencies (Ministries) IT systems and b) coordination of cybersecurity activities of critical infrastructure and defense infrastructure agencies. The Monitoring function is a direct function for NISC whiles the coordination function is remote. Such a structure gives a better result than merely assigning the responsibility to a single Ministry. Below is the functional structure of NISC.
Figure 1: Functional Structure of NISC
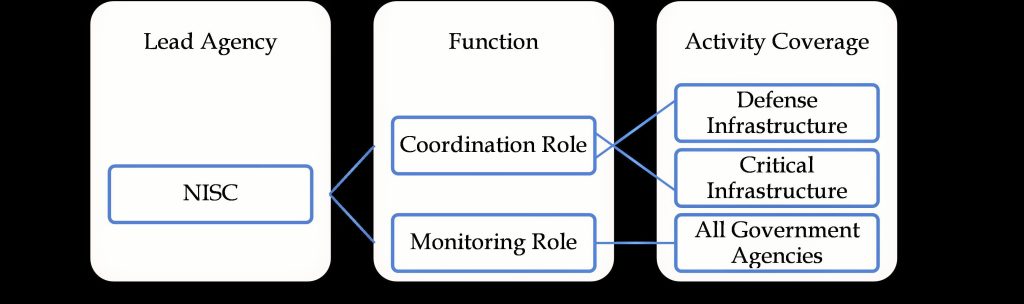

It is expected that the National Cybersecurity Center that the President said is to be established for cybersecurity activities would have the NISC structure. The center must also be headquartered at the office of President since their job coverage covers defense and also critical infrastructure.
- The next thought relates the proper targeting of cyber risks. One noticeable challenge in cybersecurity policy design even in advanced countries has been the overconcentration of efforts on protecting critical infrastructure. Many policies and strategies often are concerned about the protection of critical infrastructure for apparent reasons. The overconcentration leads to total abandonment of equally important players in the ecosystem. The cyberspace has four groups who are affected in the event of an attack. They are; the citizens, the government agencies, small and medium companies (SMEs) and finally big companies. Each of the players assumes a different level of risk and financial investment in cybersecurity. The level of exposure determines the amount of investment each group within the cyberspace makes in cybersecurity. Obviously, the government and providers of critical infrastructure (big Companies) would invest in cybersecurity measures owing to the relevance of IT to their businesses. Many of the cybersecurity policies have focused on the big companies and the government agencies at the expense of citizens and SMEs protection. When one carefully examines the four players from the risk and investment tradeoff, it becomes clear that the weak links are noticeable in the citizens and the SMEs. There is little investment by SMEs and citizens in cybersecurity infrastructure, and at the same time, they also face significant risk especially in the wake high reliance on the internet. Below is a situational risk matrix for the four players in the cyberspace.
Figure 2: Risk/Investment Matrix
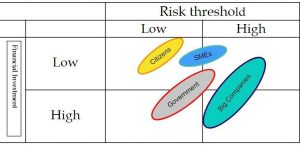

It is evident that the most vulnerable to cybercrimes are the ordinary citizens and the SMEs. Any policy and strategy must, therefore, concentrate efforts more at reducing their risk threshold.
- The third thought has to do with the defining doctrine of the NCSPS. A well-defined dogma is always essential and critical for the functioning of any plan, policy or strategy. Scholarship on regulatory approaches to cybersecurity has identified four principal doctrines that differ in goals and means. Namely, these are the doctrine of prevention, the doctrine of risk management, the doctrine of deterrence through accountability, and the doctrine of public cybersecurity. The first seeks to create fail-proof systems by thorough testing and standardization, the second acknowledges that is impossible to prevent all attacks and focuses its resources on reducing expected losses and securing critical nodes in the system, the third one uses surveillance to monitor the information environment and punish those who commit cyber crimes, and the fourth seeks to create a conducive environment where everyone has a proactive role in monitoring cyber threats and increasing the system’s security. Pursuing a mixed regulatory approach inspired by the doctrine of public cybersecurity where a distinction is made between companies that operate critical infrastructures and those who do not, in my opinion, offers more benefit to Ghana than the other dogma. This regulatory approach, however, would work well with accompanying measures such as the general Baseline Cybersecurity Framework- [that lists best practices and relevant standards in cybersecurity], and a Liability and Incentives Scheme- [which will allow companies to choose a security level of compliance to access different levels of incentives].
- My fourth thought concerns the precise definition of the objectives of the policy. Key to the success of the cybersecurity policy and strategy just like any other policy is how the overall objective(s) of the policy is framed. Our ability to flesh out measurable objectives with clearly defined activities would go a long way in ensuring a better outcome. Here, I suggest that the objectives must include the development and advancement of free, fair and secure cyberspace that guarantees total security for Ghanaians. It must also contribute to the socio-economic progress of Ghana and finally contribute to international peace, stability and national security efforts.
- The fifth thought is that cybersecurity policy and strategy must be Ghana own [made in Ghana]. One challenge that many programmes and projects have suffered from in the past is ownership. Projects and programmes which are donor driven often suffer ownership and sustainability challenges. It is vital that the Cybersecurity arrangement of Ghana is Ghanaian owned and driven by Ghanaians. The support from the WB and other bilateral and Multilateral Development Partners (DPs) must not be construed to mean arrogation of responsibility to them. Sustaining the cybersecurity efforts would very much depend on how well we navigate DP’s interest in line with the broad Ghanaian interest. Ghana must own the process and only recourse to DPs when it becomes highly necessary.
I conclude by commending the government for the initiative to protect its cyberspace. I also encourage the government to expand the scope of consultations given that cybersecurity matters are trans-sectorial. It is also critical that the processes are driven by Ghanaians to ensure sustainability. Having a dedicated body to lead the process is a right way to go.
From the same author: SUSTAINING NIEP WOULD REQUIRE A MULTIFACETED APPROACH
Author: Henry, KYEREMEH


